Every time I see a new cyber incident on the news, or start working on a new incident, the first question that pops up in my mind (much like many other Digital Forensics and Incident Response (DFIR) professionals) is
How did they get in?!
That innate human characteristic of curiosity (and a bit of nosiness) creeps up and one of the most frustrating parts about the DFIR profession is not getting to the root cause of initial access.
What is Initial Access?
Initial access into a corporate network is the cornerstone of any cyber-attack and stands to be the most difficult stage of the attack chain. Cybercriminals will use various tactics and techniques to achieve any level of access into a network including phishing, exploitation of vulnerable systems and other social engineering mechanisms.
The combination of strong technical, human and procedural controls are essential to combating the tactics and techniques deployed by threat actors. These controls include:
Technical:
- Effective firewall configuration
- Intrusion detection and prevention systems
- Multi-factor authentication
- Endpoint protection
People:
- Increased awareness to cyber risk
- Good password hygiene
Procedural:
- Effective vulnerability management and patching schedules
- Threat modelling
- Penetration-testing and red-team operations
Initial Access Brokers
Initial access is so valuable and crucial for conducting cyber-attacks that certain cybercriminals focus solely on acquiring and profiting from access into corporate environments. These cybercriminals are known as Initial Access Brokers (IABs) and use dark web marketplaces to sell access to other cybercriminals including ransomware operators. In most cases, IABs will acquire compromised credentials for Remote Desktop Protocol (RDP) or Virtual Private Networks (VPN) used in corporate environments. With the increase in remote working, these technologies are now widely used by almost every employee in most organisations.
IABs have become a valuable part of the Ransomware-as-a-Service (RaaS) economy. By using IABs, ransomware operators effectively outsourced the reconnaissance and initial access groundwork, consequently reducing the time and effort needed to target their victims. The time period between the initial access compromise by the IAB and the execution of ransomware and data exfiltration by the ransomware operator, can be weeks, months or even years. This makes it extremely challenging for incident responders to correlate both compromises and attribute malicious activity to a specific threat actor.
Based off research by KELA, an Israeli Cyber Threat Intelligence firm, in Q1 2023, more than 600 network access listings were for sale across the dark web, with a cumulative requested price of around USD$580,000.
There was an increase of 15% in the number of listings but a decrease of 50% in cumulative requested price compared with Q1 2022, meaning more supply with lower prices for prospective threat actors.
Examples of IABs postings:
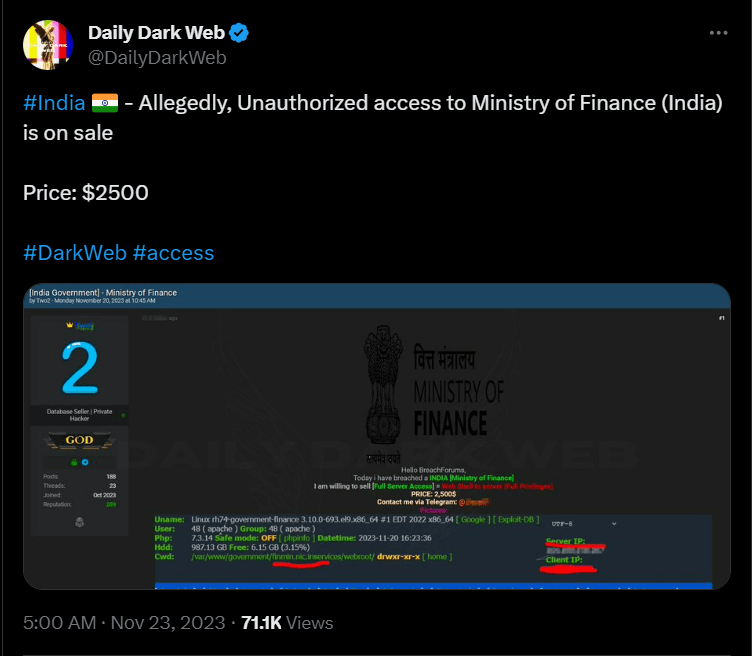
Source: https://twitter.com/DailyDarkWeb/status/1727386462323421341
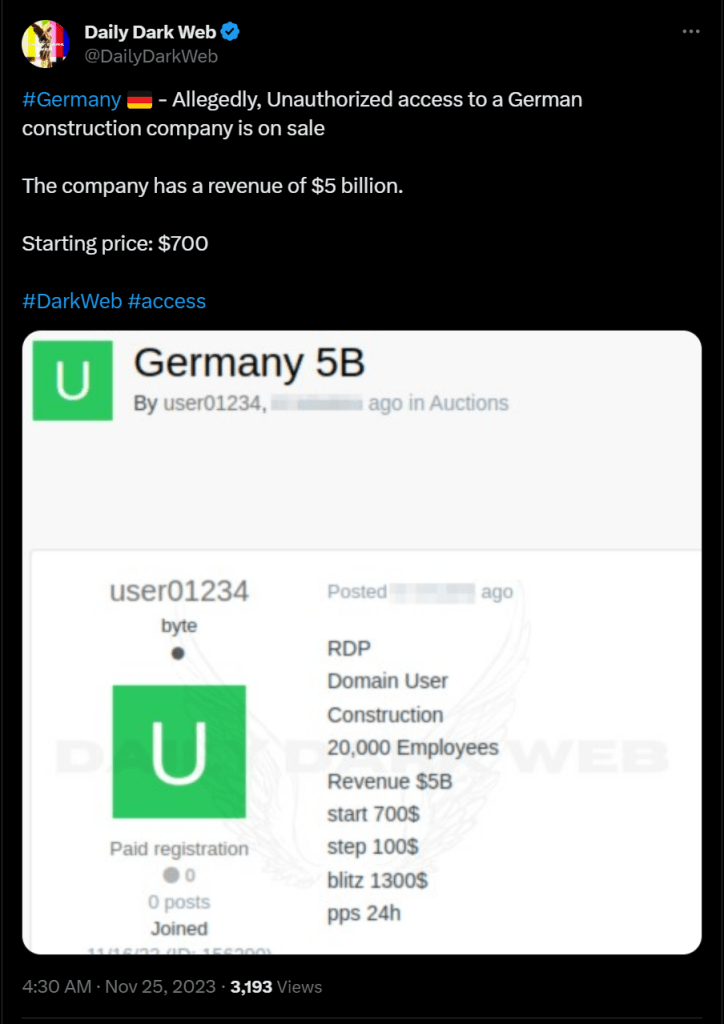
Source: https://twitter.com/DailyDarkWeb/status/1728103689771184378
How can Cyber Threat Intelligence help protect organisations against IABs?
In addition to standard cybersecurity best practices, Cyber Threat Intelligence (CTI) is a proactive approach that involves the aggregation, analysis and distribution of information regarding cybercrime. CTI is a valuable and significant data source that enables organisations to protect against major incidents or breaches even after an initial access compromise. Effective and thorough CTI practices can provide insights that are:
- Organisation-specific, rather than general security advisories and publicly available information. CTI can provide precise potential initial attack vectors into an organisations network based of their attack surface. This can include breached credentials, unknown publicly-facing infrastructure or third-party supply chain attacks.
- Detailed and contextual, which can highlight adversarial tactics, techniques and procedures used by specific threat actors and what they leverage to gain initial access.
- Actionable, giving security teams and IT personnel the ability to proactively prioritise and remediate threats and also identify paths of lateral movement within a network to contain the impact of an incident after an initial compromise.
Further Reading:
- https://www.kelacyber.com/wp-content/uploads/2023/04/KELA_Research_Q1-2023_ransomware-and-network-access-sales.pdf
- https://socprime.com/blog/what-is-initial-access-mitre-attck-initial-access-tactic-ta0001/
- https://www.sentinelone.com/blog/more-evil-markets-how-its-never-been-easier-to-buy-initial-access-to-compromised-networks/
- https://www.recordedfuture.com/initial-access-brokers-key-to-rise-in-ransomware-attacks
- https://www.nsbcyber.com/library/iabs-targeting-australian-companies

Leave a reply to Week 49 – 2023 – This Week In 4n6 Cancel reply